If you’re searching for websites that accept guest posts or articles related to “Computer Viruses,” you are at the right place.
TSR will help you with guest contributions and publish articles related to computer viruses. Before submitting your content, make sure to read the website’s submission guidelines carefully.

A computer virus is a spiteful program or malware that contaminates the operating system of electronic systems such as computers or smartphones.
This program will enter your system by being embedded within the ordinary file as a code. When you run the file, the “infectious” action of the virus deploys. So, to Write For Us, you can email us at contact@techsupportreviews.com
These viruses can be used for anything from simple jokes to personal information or to destroy files and computers.
Users may not notice this type of process. Hence, it is important to protect devices‘ operating systems with programs called “antivirus.”
Characteristics of computer viruses
- They remain dormant in the device’s RAM, even when the program is not executing.
- They infect the files on the hard drive.
- They spread to other devices by sharing files.
- They are executable; they parasitically host in other programs they run.
- They run or act only when the scheduled conditions have been met, for example, a specific date or when getting a certain number of replications on the device.
- They affect or make the development of the team impossible.
- Each virus has a specific goal: to slow down computers, destroy files, obtain secret information (e.g. bank details), etc.
- They mutate every other time, which makes them difficult to detect.
Types of computer viruses
There is a wide variety of computer viruses. Still, these can group widely into viruses that affect files, called direct-acting viruses, and viruses that affect the device’s boot, called resident viruses. The third type of virus, called the Multipartite type, has been added to this pair.
- According to their goals and methods, the types of viruses are usually best known by the following names:
- Trojans, also called Trojan horses, intend to obtain personal information from the user without the user detecting it by inadvertently entering the system.
- Backdoors: A “backdoor” allows a third party to introduce infected files into the system. It is similar to a Trojan.
- Boot virus or boot virus: Starts when you boot the operating system.
- Time bombs: that silently reside in the system and are activated only from a moment programmed by their creator.
- Macro viruses are embedded in files containing the macro, particularly doc, xls, and ppt.
- Worms replicate within the computer system and spread through the Internet (email), infecting anyone who receives messages from the infected account.
- Hijackers are a class of virus that controls the Internet browser, change the home page, add pop-up advertising, install tools in the bar without the user’s consent, and, finally, prevent access to specific web pages.
- Keyloggers are viruses that capture the key and run without notice to reveal what the user types on the screen. They are mainly used to obtain passwords.
- Zombie refers to viruses that allow remote computer control by a third party.
How to Submit Your Article to Tech Support Reviews?
To Write for Us, you can email at contact@techsupportreviews.com
Why Write For Us at Tech Support Reviews 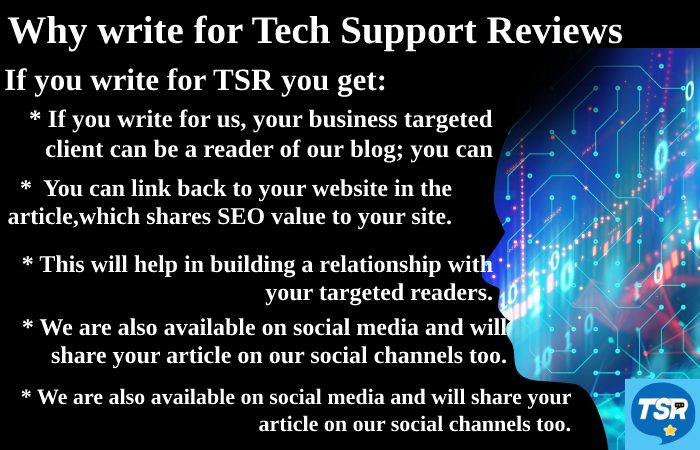
So, To Write for Us, you can email at contact@techsupportreviews.com
Search Terms Related To Computer Virus Write For Us
Computer virus
Malware
Trojan horse
Worm
Computer virus symptoms
Spyware
Rootkit
Botnet
Phishing
Virus protection
Antivirus software
Cybersecurity threats
Virus removal
Virus scan
Computer virus history
Computer virus types
Ransomware
Computer virus news.
Adware
Computer virus symptoms
Computer virus prevention
Boot Sector Virus
Overwrite Virus
Direct Action Virus
Web Scripting Virus
Polymorphic Virus
Directory Virus
Macro Virus
Memory Resident Virus
Companion Virus
Multipartite virus
Search Terms Related For Computer Virus Write For Us
“Submit a guest post” + “Computer Virus”
“Write for us” + “Computer Virus”
“Guest blogging” + “Computer Virus”
“Contribute to our site” + “Computer Virus”
“Guest post guidelines” + “Computer Virus”
“Become a contributor” + “Computer Virus”
“Submit an article” + “Computer Virus”
“Article submission guidelines” + “Computer Virus”
“Write for our blog” + “Computer Virus”
“Guest writer” + “Computer Virus”
“Submit content” + “Computer Virus”
“Bloggers wanted” + “Computer Virus”
“Guest posting opportunities” + “Computer Virus”
“Contribute an article” + “Computer Virus”
“Guest blogging guidelines” + “Computer Virus”
“Submit a blog post” + “Computer Virus”
“Article submission guidelines” + “Computer Virus”
“Write for our website” + “Computer Virus”
“Blog contributions” + “Computer Virus”
“Guest blog post” + “Computer Virus”.
Guidelines of the Article – Computer Virus Write For Us
To submit an article, please email us at contact@techsupportreviews.com with the subject “Guest Post for Techsupportreviews Site. Our publication team will contact you within 12 hours.
Related Pages:

